From Single Intrusion to Double Extortion – Cyberattack on Change Healthcare

The impact of cyberattack which was aimed at Change Healthcare 3 months ago, disrupted the daily claim processing activities of at least 80% of U.S. hospitals, 60% of pharmacies, and many more patients, is still dealt by major healthcare networks in the industry. United Healthcare and its subsidiaries which fell prey to this attack are one of nation’s largest healthcare providers. The direct victim ‘Change Healthcare’ – the largest payment exchange platform operator, initiated a damage controlling maneuver by temporarily shutting down their payment platform causing a system outage for users; This in turn contributed to the stalling of nationwide claim processing.
United Health Group (UHG) – A health insurance giant, considered to be the world’s largest healthcare company by revenue with 440,000 employees operates in all 50states. Optum Inc. was formed as a subsidiary of UHG in 2011 to operate as a unit of UHG, started performing well – accounting for 44% of UHG’s profits in 2017. Optum’s success lead UHG to merge with Change Healthcare LLC in 2022 for an estimated deal of $13 billion including the $5 billion debt settlement. Change Healthcare – being a healthcare data & analytics giant, this merger allowed Optum & UHG to gain access to data coming from 15 billion annual healthcare transactions.
On 21st of February several healthcare users of Change Healthcare systems experienced a countrywide outage. Change Healthcare displayed an error message and kept on updating the situation status from 02:15 EST via a dedicated webpage.
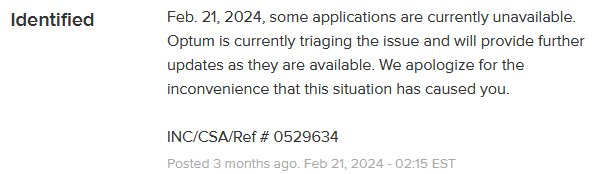
The initial status error message displayed by Change Healthcare
At 14:09EST Change Healthcare admitted that it is experiencing a network interruption due to a cyber security issue. The next update stated Change Healthcare had to disconnect its systems when they became aware of an outside threat; thereby protecting its partners and patients from the impact.
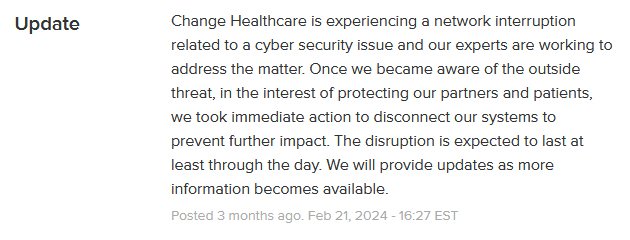
Notification of Cyberattack & disconnection of systems
Many healthcare security experts, healthcare medias and Optum believed nation-state/states were behind the attack.
On February 22nd, American Hospital Association(AHA) advised healthcare organizations to exercise precautions by disconnecting from Optum and from unavailable applications specified by Change Healthcare, until it is found safe to reconnect.
 On February 19th, Screenconnect – A remote monitoring and management software developed by ConnectWise (A platform & a software company built for software and services for TSPs) addressed a similar threat and advised its users of the vulnerabilities and recommended to upgrade their software to the latest release. The users of the affected version of software were probable to face both the first vulnerability which allows the hackers to remotely gain access to the systems with administrator privileges, and the second one in which case, the hackers could upload a malicious file to gain access to the corrupted system.
On February 19th, Screenconnect – A remote monitoring and management software developed by ConnectWise (A platform & a software company built for software and services for TSPs) addressed a similar threat and advised its users of the vulnerabilities and recommended to upgrade their software to the latest release. The users of the affected version of software were probable to face both the first vulnerability which allows the hackers to remotely gain access to the systems with administrator privileges, and the second one in which case, the hackers could upload a malicious file to gain access to the corrupted system.
Many healthcare security professionals saw similarities, thus made them believe the attackers of Screenconnect incident exploit the vulnerability to pass through Change Healthcare systems. Being uncertain about the nature of Change Healthcare attack, the spokesperson of ConnectWise had told Becker’s that they cannot confirm a direct connection between Screenconnect and Change Healthcare incident, pointing to the fact that Change Healthcare is not a direct customer of ConnectWise, nor any reports received from service partners pertaining to the healthcare attack on February 21st. A week later, the actual threat actors denied the belief based on connecting the two incidents, when they attempted to claim responsibility and disclose their identity.
On February 28th, a cyber ransomware gang called ‘BlackCat/ALPHV’ claimed responsibility for the cyberattack on Optum-Change Healthcare, by publishing the claim on their dark web leak site. This cyber crime gang, which is believed to share links with Russia, had also claimed that they had stolen 6TB of data from Change Healthcare network supposedly belongs to thousands of healthcare providers, payers, pharmacies and patients.
The gang shook the entire industry by claiming, that they stole source code for Change Healthcare solutions, and sensitive information belonging to partners including U.S. military’s Tricare healthcare program and Medicare federal health insurance program.
According to BlackCat/ALPHV’s claim, the stolen data about millions of people, could be a composition of information including medical records, insurance records, dental records, payments information, claims information, and personally identifiable information(PII) of patients and active U.S. military/navy personnel.
While the intruders started the attack on 21st of February by encrypting data and making the systems unavailable for employees, the cyber intrusion happened on 12th of February using stolen employee credentials to access Citrix portal – an application by Change Healthcare to enable remote access. The type of attempt used in stealing the employee credentials was later attributed to the usage of information-stealing malware.
The intruders were dormant for 10 days but having access to the entire network and data before deploying the ransomware on 21st. The Citrix portal not having an MFA (Multi-Factor Authentication) was seen as one of the reasons for it to easily compromise its entrance.
 Blackcat cyber crime gang – surfaced in November 2021, was supposedly believed by many FBI agents to be a rebrand of Darkside and Blackmatter ransomware groups – both seized by law enforcement agencies.
Blackcat cyber crime gang – surfaced in November 2021, was supposedly believed by many FBI agents to be a rebrand of Darkside and Blackmatter ransomware groups – both seized by law enforcement agencies.
The flash alert released by FBI in April 2022, stated that Blackcat has breached at least 60 organizations worldwide, between its launch in November 2021 and March 2022. According to FBI, as of September 2023, Blackcat has raked over $300 million as ransom from 1000+ victims worldwide.
In December 2023, FBI breached the Blackcat’s ransomware servers and monitored their activities. Through a confidential human source, who was staged to perform as Blackcat’s affiliate, FBI managed to obtain the login credentials to ALPHV’s backend affiliate panel. This disrupted the operations of Blackcat and ended up in FBI shutting down Blackcat’s previous TOR leak site. Despite Blackcat regained access to the site, it was deemed useless as the site could now be accessed by both FBI and Blackcat due to the credential leak. Hence Blackcat now operates a new TOR leak site.
PS: The U.S. State Department is now offering a reward up to $15 million, for information that could help locating the leaders of Blackcat or individuals affiliated to the gang.
Following the disruption of Blackcat’s operation by FBI in December 2023, a post been published by Blakcat administrator encouraging its affiliates to target hospitals. FBI & CISA(Cybersecurity and Infrastructure Security Agency) believes the response for this post could be the reason behind Change Healthcare attack, and warns more Health sector focused attacks in future.
FBI analysis further indicates, since December 2023, healthcare sector been the commonly victimized among the 70 leaked victims of Blackcat. Taking this into account, on February 29th, FBI released an advisory to warn healthcare sectors and hospitals to beware of cyberattacks.
Although, Untied Health CEO Andrew Witty’s testimony confirmed that UHG paid ransom, the actual amount was never disclosed to the press. What patches this missing information is the message circulated by the affiliate who coordinated the Change Healthcare attack, confirming that Blackcat received a ransom of $22 million in Bitcoin on 1st of March from UHG, but failed to pay their share and have banned them from the operations. The affiliate identified themselves as “Notchy” and accused Blackcat of stealing $22 million. Notchy claimed they still have 4TB of critical data for which they feel pity for Optum. However, on 8th of April, Ransomhub (another cybercrime gang) issued a statement on their data leak site – the stolen data from Change Healthcare’s February attack will be released if UHG did not reach a deal. This was believed by the experts to be the outcome of Notchy switching sides and joining Ransomhub.
On April 15th, Ransomhub shared screenshots of stolen data from February attack, extorting UHG to pay them in 5 days, otherwise the data shall be sold to the highest bidder. An update from Bleeping Computer states that UHG confirmed it paid a ransom in order to protect the data from cyber criminals. Bleeping computer writes, that it checked the Ransomhub’s data leak site and found UHG’s name was removed from victims’ list.
Cyber crime investigation officers attribute this double extortion to Blackcat’s “exit-scam trick” performed on United Health Group.
On May 7th, UHG updated its dedicated status page – that the incident pertaining to February cyber-attack was resolved. The page also indicates that the restoration is in progress for Change Healthcare products & services.
The progress updates could be tracked via a cyber response page: https://www.unitedhealthgroup.com/changehealthcarecyberresponse
A recent survey administered by American Medical Association (AMA), found that:
- 77% of respondents have experienced service disruption and are still feeling the effects of the cyberattack.
- 80% have lost revenue from unpaid claims.
- 51% have lost revenue due to the inability to charge patient co-pays/ remaining obligation.
- 55% had to use personal funds to cover practice expenses.
United Health Group is closely monitoring the dark web leaks sites of cyber criminals and has reported no additional divulging of data observed other than the screenshots which were released in mid-April.
UHG has also launched a “Temporary Funding Assistance Program for Providers” which is designed to bridge the gaps in short-term cash-flow needs of providers who are impacted by the cyber-attack.
With dozens of lawsuits to face, the cyber-attack caused United Health Group, a $872 million hit on its first quarter earnings, which is expected to rise over $1 billion.

